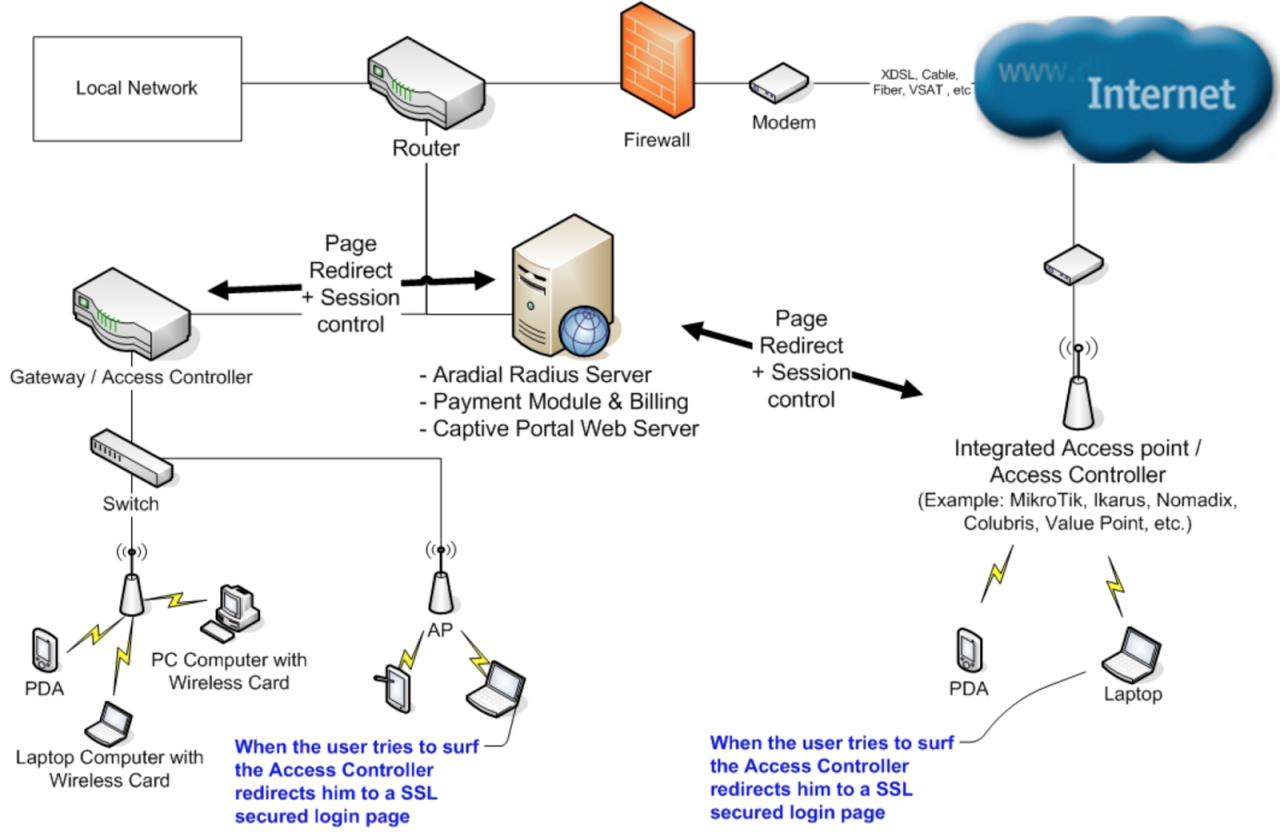
Radius server, a cornerstone of network security, acts as a central authentication and authorization system for users accessing network resources. It plays a critical role in controlling access to sensitive information and services, ensuring only authorized individuals can utilize network resources.
The Radius server sits at the heart of network security, acting as a gatekeeper for users attempting to connect to network resources. It enforces access control policies, verifying user identities and granting or denying access based on pre-defined rules. This centralized approach simplifies security management, allowing administrators to easily manage user permissions and enforce consistent security policies across the entire network.
Radius Server Standards and Protocols
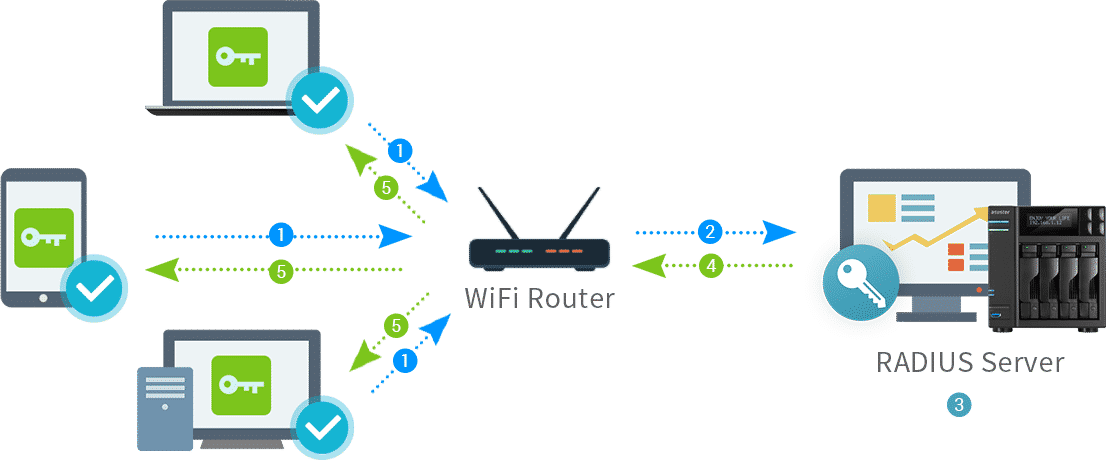
The RADIUS protocol is a networking protocol that provides centralized authentication, authorization, and accounting (AAA) services for network access. It is widely used in various network environments, including wired and wireless networks, VPNs, and dial-up connections.
The Radius Protocol, Radius server
The RADIUS protocol is based on a client-server architecture. The RADIUS server acts as a central point for managing user authentication and authorization, while the RADIUS client, typically a network device like a router or switch, communicates with the server to authenticate users and enforce access policies.
- Authentication: The RADIUS server verifies the identity of a user attempting to access the network by checking their credentials against a database of authorized users. This can involve validating usernames and passwords, verifying digital certificates, or using other authentication methods.
- Authorization: Once a user is authenticated, the RADIUS server determines the user’s access privileges, such as which network resources they can access and what actions they are permitted to perform.
- Accounting: The RADIUS server tracks user activity, such as the time of login and logout, the amount of data transferred, and the resources accessed. This information can be used for billing, security auditing, and network performance monitoring.
Different Versions of the Radius Protocol
The RADIUS protocol has evolved over time, with different versions released to address new requirements and enhance functionality.
- RADIUS Version 1: The original version of the RADIUS protocol, released in 1991. It provides basic authentication, authorization, and accounting capabilities.
- RADIUS Version 2: Released in 1999, RADIUS Version 2 introduced several enhancements, including support for encryption, improved security, and extended attribute support.
- RADIUS Version 3: The latest version of the RADIUS protocol, released in 2005. RADIUS Version 3 offers further security improvements, enhanced scalability, and support for new authentication and authorization mechanisms.
Role of the Radius Standard in Network Security
The RADIUS protocol plays a crucial role in network security by providing a centralized point for managing user access and enforcing security policies.
- Centralized Authentication: By centralizing authentication, RADIUS servers help to streamline the process of managing user accounts and access privileges. This makes it easier to enforce consistent security policies across the network.
- Strong Authentication: RADIUS servers support various authentication methods, including password-based authentication, digital certificates, and multi-factor authentication. This helps to ensure that only authorized users can access the network.
- Access Control: RADIUS servers allow administrators to define granular access control policies that specify which users can access specific network resources. This helps to prevent unauthorized access and data breaches.
- Auditing and Reporting: RADIUS servers track user activity and generate detailed audit logs. This information can be used to identify security incidents, monitor network usage, and improve security practices.
Closure: Radius Server
Understanding the intricacies of Radius server operation is essential for any organization seeking to maintain a secure and reliable network. From its core functionalities to its integration with various network systems, Radius server offers a comprehensive solution for managing user access and enforcing network security policies. By embracing the power of Radius, organizations can confidently navigate the complexities of modern network security, safeguarding their valuable data and resources.
Radius servers are essential for network authentication and authorization, but they can sometimes feel a bit dry. If you’re looking for a creative outlet, check out these christmas tree craft ideas for a fun break from the technical world.
Once you’ve finished crafting, you can return to the rewarding task of securing your network with a robust radius server setup.