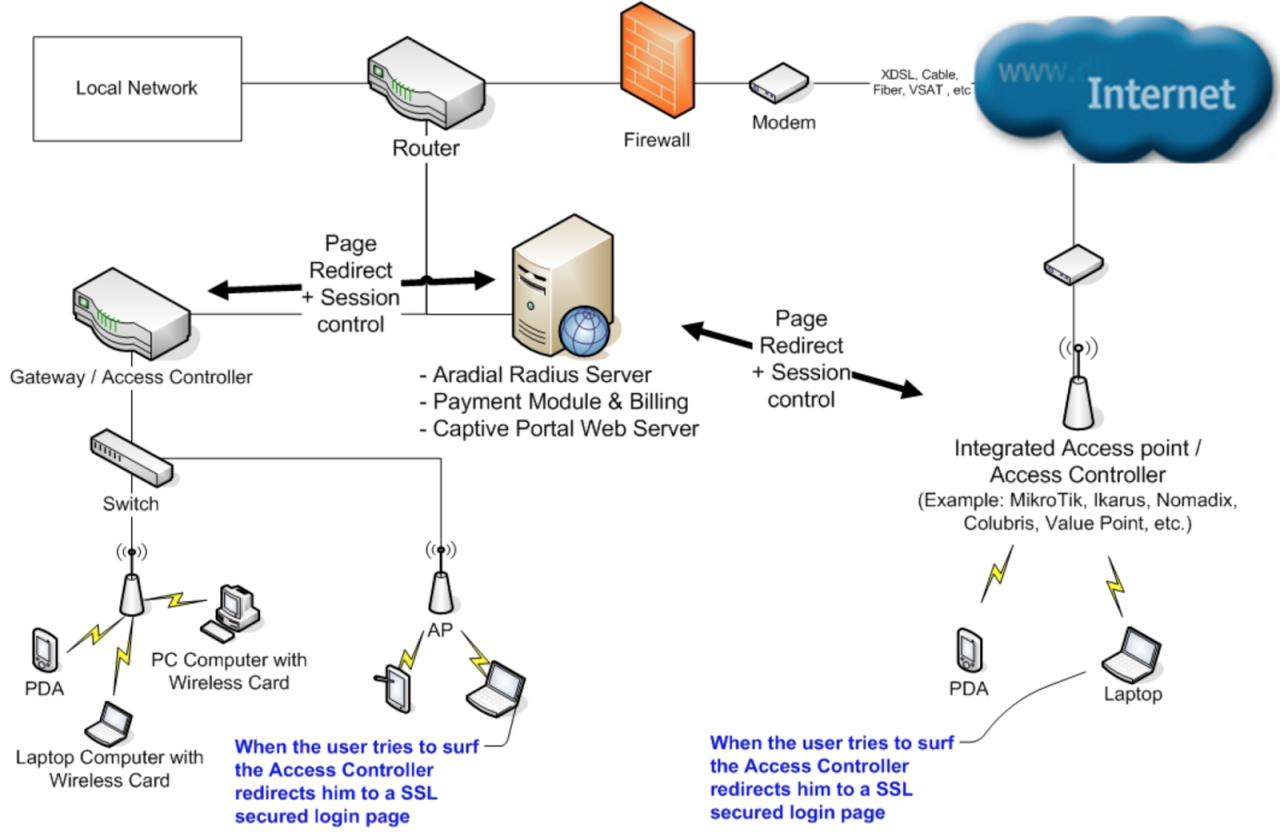
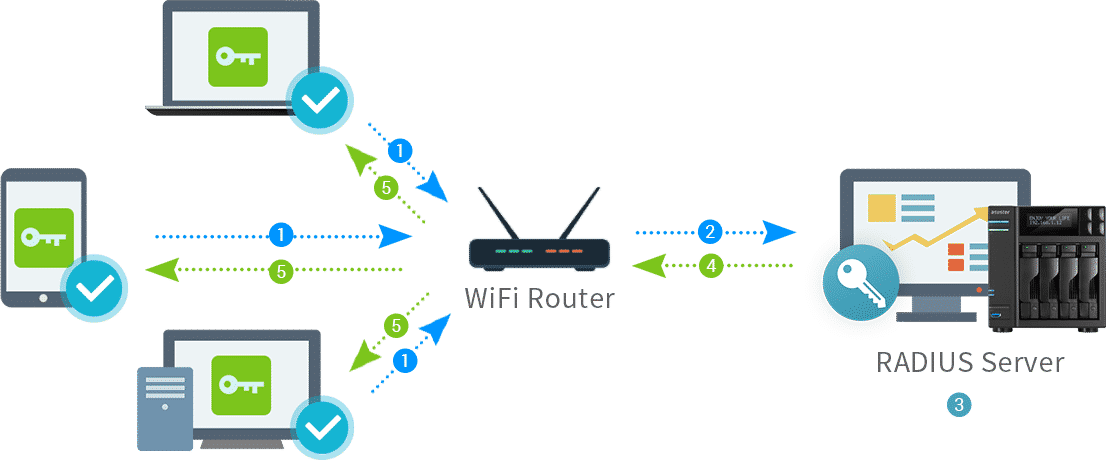
Active hosts, the pulsating heart of any network, are the devices actively participating in communication and data exchange. From servers tirelessly serving web pages to workstations humming with user activity, these devices drive the digital world.
This comprehensive guide delves into the multifaceted world of active hosts, exploring their identification, monitoring, security, management, and optimization. We’ll unravel the intricate workings of network communication, discover the applications powered by active hosts, and delve into the evolving trends shaping their future.
Active Host Identification
Active host identification is a crucial aspect of network security and administration. It involves identifying devices or systems that are currently active and communicating on a network. This information is essential for various purposes, including network mapping, vulnerability assessment, security auditing, and troubleshooting.
Methods for Identifying Active Hosts
Several methods can be employed to identify active hosts on a network. These methods are categorized as either passive or active, depending on their approach. Active methods actively probe the network to identify hosts, while passive methods rely on observing network traffic.
- Network Scanning: Network scanning involves sending packets to a range of IP addresses to determine which addresses are associated with active hosts. This method is often used to identify all devices on a network, regardless of their operating system or services.
- Port Scanning: Port scanning is a specialized form of network scanning that focuses on identifying open ports on a host. This information can be used to determine the services running on a host and identify potential vulnerabilities.
- Ping Sweeps: Ping sweeps are a simple form of network scanning that involves sending ICMP echo requests to a range of IP addresses. If a host responds to the ping request, it is considered active. This method is primarily used to quickly identify active hosts on a network.
Tools and Technologies for Active Host Identification
Several tools and technologies are available to assist in active host identification. These tools provide various functionalities, including network scanning, port scanning, and data analysis.
- Nmap (Network Mapper): Nmap is a powerful open-source tool for network scanning and security auditing. It offers a wide range of features, including port scanning, OS detection, and vulnerability scanning. Nmap is highly versatile and can be used for various purposes, from network mapping to security assessments.
- Wireshark: Wireshark is a popular network protocol analyzer that captures and analyzes network traffic. It can be used to identify active hosts by examining network traffic patterns. Wireshark is a powerful tool for troubleshooting network issues, analyzing security incidents, and understanding network behavior.
- Ping: Ping is a basic network utility that sends ICMP echo requests to a host. If the host is active, it will respond to the ping request. Ping is a simple and quick way to determine if a host is reachable.
Process of Identifying Active Hosts
The process of identifying active hosts typically involves the following steps:
- Define the network scope: Determine the range of IP addresses to be scanned or the specific network segments to be analyzed.
- Select appropriate tools and methods: Choose the most suitable tools and methods based on the desired level of detail and the specific objectives.
- Execute the scan or analysis: Use the selected tools and methods to scan the network or analyze the traffic.
- Analyze the results: Interpret the scan results or traffic analysis to identify active hosts and their characteristics.
- Document the findings: Record the identified hosts and their associated information for future reference and analysis.
Active Host Management
Active host management is a critical aspect of maintaining a healthy and efficient IT infrastructure. It encompasses the tasks and processes involved in overseeing, configuring, and optimizing active hosts within a network. This involves managing the lifecycle of these hosts, from their initial provisioning to their eventual decommissioning.
System Administrators’ Role, Active host
System administrators play a central role in managing active hosts. Their responsibilities include:
- Provisioning: This involves setting up new hosts, including installing operating systems, configuring network settings, and installing necessary software.
- Configuration: System administrators configure hosts to meet specific requirements, such as security settings, resource allocation, and application deployment. This involves setting up user accounts, defining access permissions, and configuring software packages.
- Maintenance: This includes tasks like applying security patches, updating software, monitoring system performance, and troubleshooting issues. It also involves backing up data and ensuring data integrity.
Active Host Management Approaches
There are various approaches to managing active hosts, each with its own advantages and disadvantages.
- Centralized Management Platforms: These platforms provide a single point of control for managing multiple hosts. They offer features like centralized configuration, automated provisioning, and remote management capabilities. Examples include Microsoft System Center Configuration Manager (SCCM), VMware vCenter Server, and Red Hat Satellite.
- Automation Tools: Automation tools can streamline repetitive tasks, such as software deployment, configuration updates, and security patching. They reduce manual effort and improve efficiency. Examples include Ansible, Puppet, and Chef.
Common Tasks
Active host management involves a wide range of tasks. Here are some common ones:
- Host Discovery: Identifying and tracking all active hosts within a network.
- Inventory Management: Maintaining a detailed inventory of hardware and software components on each host.
- Patch Management: Regularly applying security patches and software updates to mitigate vulnerabilities.
- Performance Monitoring: Tracking system performance metrics, such as CPU utilization, memory usage, and disk space.
- Resource Allocation: Managing and allocating resources, such as CPU, memory, and storage, to ensure optimal performance.
- Security Management: Implementing security measures, such as firewalls, intrusion detection systems, and access control policies.
- Backup and Recovery: Regularly backing up data and implementing disaster recovery plans to protect against data loss.
- Troubleshooting: Diagnosing and resolving system issues, such as network connectivity problems, application errors, and hardware failures.
Active Host Trends
The landscape of active hosts is undergoing a dynamic transformation, driven by the emergence of groundbreaking technologies such as cloud computing, edge computing, and the Internet of Things (IoT). These trends are reshaping how active hosts are managed, secured, and optimized, ushering in a new era of enhanced performance and scalability.
Impact of Cloud Computing
Cloud computing has revolutionized active host management by enabling flexible and scalable infrastructure. This approach allows organizations to access computing resources on demand, eliminating the need for significant upfront investments in hardware. The cloud offers a pay-as-you-go model, enabling businesses to scale their resources up or down as needed, ensuring optimal resource utilization and cost efficiency. This dynamic nature also allows for rapid deployment and configuration of active hosts, streamlining the overall management process.
Impact of Edge Computing
Edge computing is emerging as a critical component of active host management, particularly in scenarios demanding low latency and high bandwidth. This approach involves processing data closer to the source, reducing the reliance on centralized data centers and enhancing real-time responsiveness. Edge computing is particularly relevant for applications such as autonomous vehicles, industrial automation, and real-time data analytics, where swift data processing is paramount. By distributing computing resources to the edge, active hosts can leverage localized processing power, minimizing latency and improving application performance.
Impact of the Internet of Things (IoT)
The proliferation of IoT devices is significantly increasing the number of active hosts, creating new challenges and opportunities for management. IoT devices generate vast amounts of data, necessitating efficient and scalable management solutions. Active host management systems must adapt to handle the diverse range of IoT devices, ensuring secure connectivity, data integrity, and seamless integration with existing infrastructure. The interconnected nature of IoT devices also raises concerns about security vulnerabilities, requiring robust security measures to protect against unauthorized access and data breaches.
Future Developments
The future of active host technology holds exciting possibilities. Advancements in artificial intelligence (AI) and machine learning (ML) are poised to revolutionize active host management, enabling predictive maintenance, automated resource allocation, and intelligent security protocols. AI-powered systems can analyze real-time data from active hosts to identify potential issues, predict failures, and optimize performance. This proactive approach can significantly reduce downtime, enhance efficiency, and ensure optimal system health.
Additionally, the integration of blockchain technology holds immense potential for enhancing security and trust in active host management. Blockchain’s decentralized and immutable nature can create a secure and transparent ledger for tracking device identities, data transactions, and system updates, mitigating the risk of tampering and unauthorized access.
Final Conclusion: Active Host
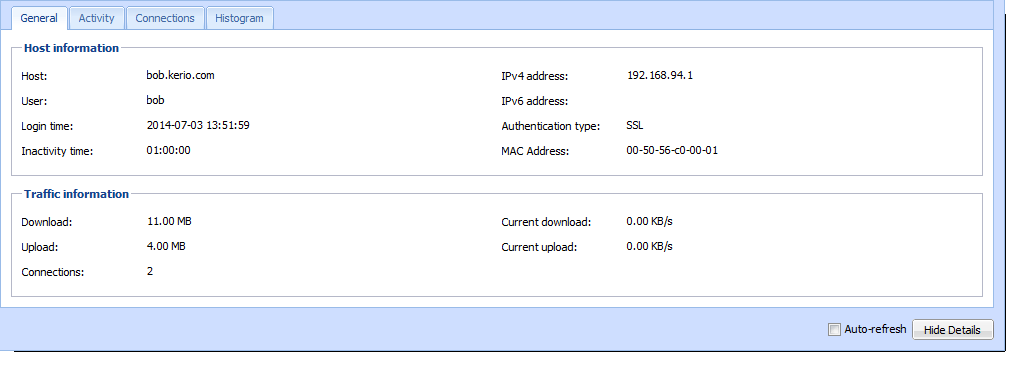
By understanding the complexities of active hosts, we gain valuable insights into network behavior, security vulnerabilities, and performance optimization strategies. This knowledge empowers us to manage networks effectively, safeguard sensitive data, and ensure optimal system performance, ultimately contributing to a more secure and efficient digital landscape.