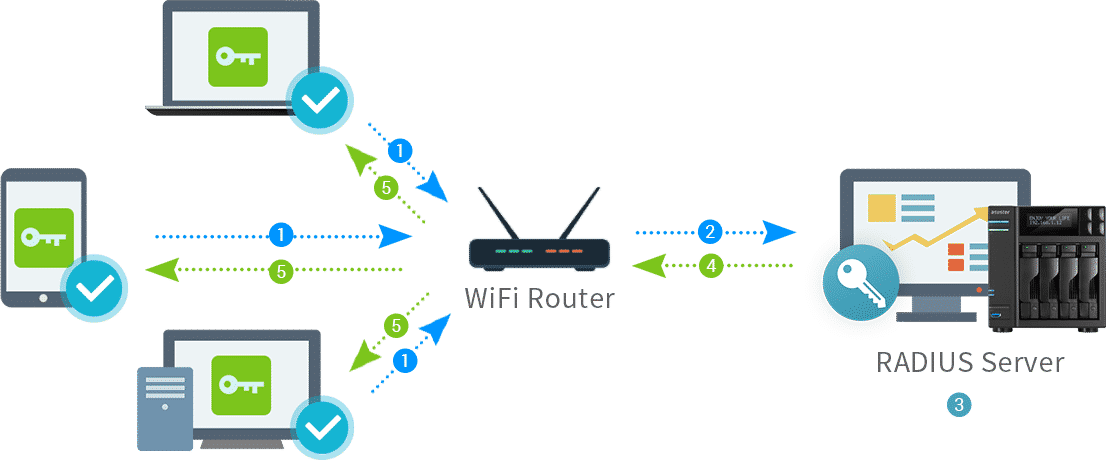
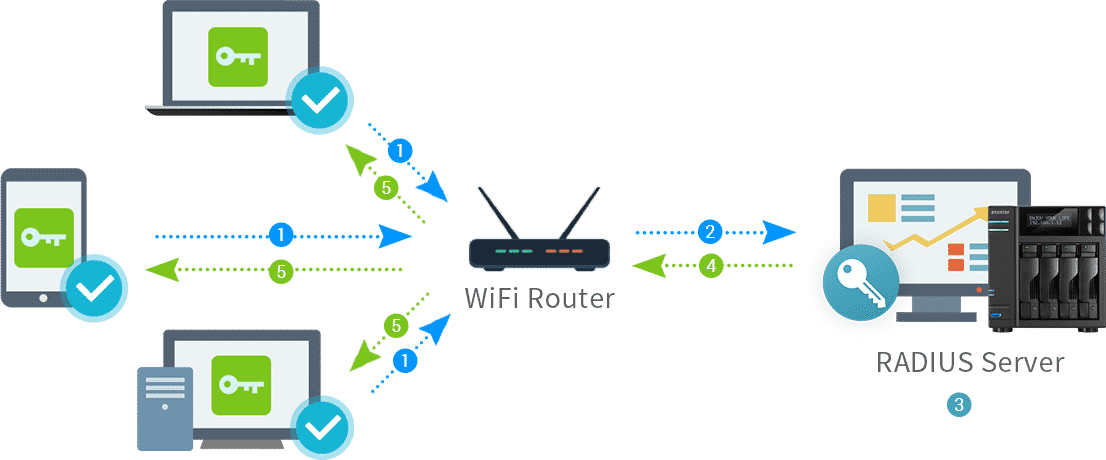
Radius Server: Network Security’s Gatekeeper, these powerful systems act as the guardians of your digital realm, meticulously controlling access and ensuring only authorized individuals can enter your network. Imagine a bustling city with a single, highly secure entrance. This entrance, akin to a Radius server, diligently verifies the identity of each person seeking entry, granting access only to those with legitimate credentials.
The Radius server stands as a cornerstone of modern network security, meticulously managing user authentication and authorization. From humble beginnings, Radius servers have evolved into sophisticated systems, playing a vital role in safeguarding sensitive data and maintaining network integrity.
Radius Server Architecture
A RADIUS server is a fundamental component of network security, providing centralized authentication, authorization, and accounting (AAA) services for users and devices accessing a network. Understanding its architecture is crucial for effective network management and security.
Components of a RADIUS Server Architecture
The RADIUS server architecture consists of several key components that work together to provide AAA services:
- RADIUS Server: This is the central server that manages user authentication, authorization, and accounting data. It receives requests from RADIUS clients, processes them, and sends responses back.
- RADIUS Clients: These are network devices such as routers, switches, wireless access points, and VPN servers that send authentication, authorization, and accounting requests to the RADIUS server.
- RADIUS Database: This stores user information, access policies, and accounting records. The database can be a dedicated database server or integrated into the RADIUS server itself.
- RADIUS Protocol: This is the communication protocol used between RADIUS clients and the RADIUS server. It defines the format and structure of messages exchanged between them.
Communication Flow between RADIUS Clients, Servers, and Network Devices
The communication flow between RADIUS clients, servers, and network devices involves a series of steps:
- Authentication Request: When a user attempts to access a network, the RADIUS client (e.g., a router) sends an authentication request to the RADIUS server. This request includes information about the user, such as their username and password.
- Authentication Response: The RADIUS server verifies the user’s credentials against its database. If the credentials are valid, the server sends an authentication response to the RADIUS client, granting access to the network. If the credentials are invalid, the server rejects the request.
- Authorization Request: Once authenticated, the user may request access to specific resources or services on the network. The RADIUS client sends an authorization request to the RADIUS server, specifying the desired resources.
- Authorization Response: The RADIUS server checks its access policies and determines if the user is authorized to access the requested resources. If authorized, the server sends an authorization response to the RADIUS client, allowing access. If not authorized, the request is denied.
- Accounting: The RADIUS server keeps track of user activity, including login times, accessed resources, and data usage. This information is stored in the RADIUS database for accounting and auditing purposes.
RADIUS Protocols
The RADIUS protocol is the primary communication protocol used between RADIUS clients and servers. It defines the format and structure of messages exchanged between them. There are different types of RADIUS protocols, each with its specific functionalities:
- RADIUS Access Request (RAR): This protocol is used for user authentication and authorization requests. It includes information about the user, such as their username and password, and the requested network resources.
- RADIUS Access Accept (RAA): This protocol is used to grant access to the network. It is sent by the RADIUS server in response to a successful authentication and authorization request.
- RADIUS Access Reject (RAR): This protocol is used to deny access to the network. It is sent by the RADIUS server in response to a failed authentication or authorization request.
- RADIUS Accounting Request (ACR): This protocol is used to collect accounting information about user activity. It includes information such as login times, accessed resources, and data usage.
- RADIUS Accounting Response (AAR): This protocol is used to acknowledge the receipt of accounting information from the RADIUS client. It is sent by the RADIUS server in response to an accounting request.
Radius Server Use Cases
Radius servers play a crucial role in network security by providing centralized authentication, authorization, and accounting for network access. They are widely used in various network environments, including enterprise networks, wireless networks, and VPNs.
Authentication and Authorization
Radius servers provide a robust and secure mechanism for authenticating and authorizing users and devices accessing the network. The process involves verifying user credentials, such as usernames and passwords, against a central database. Upon successful authentication, the Radius server grants access privileges based on pre-defined policies.
Real-World Use Cases
Radius servers are widely used in various real-world scenarios, including:
- Wireless Network Access: In enterprise networks, Radius servers authenticate users accessing wireless networks. When a user tries to connect to the Wi-Fi network, the access point sends a request to the Radius server. The server verifies the user’s credentials and grants access based on the user’s role and network policies.
- VPN Access: Radius servers are used to authenticate users accessing the corporate network via VPN. When a user connects to the VPN, the VPN server sends a request to the Radius server to verify the user’s credentials. Once authenticated, the Radius server provides the VPN server with the user’s access privileges, allowing the user to access the corporate network.
- Network Access Control (NAC): Radius servers are integral to NAC solutions, which enforce security policies based on the user’s identity, device health, and network context. When a device attempts to connect to the network, the NAC system interacts with the Radius server to verify the device’s health and grant access based on the policies.
- Dial-Up Access: Radius servers can be used to authenticate users accessing the network via dial-up connections. When a user dials into the network, the modem sends a request to the Radius server to verify the user’s credentials. Once authenticated, the Radius server provides the modem with the user’s access privileges, allowing the user to connect to the network.
Radius Server Security
Radius servers are critical components in network security, enabling centralized authentication, authorization, and accounting for network access. However, they also present potential security vulnerabilities that require careful consideration and mitigation. This section explores the security risks associated with Radius servers, discusses best practices for securing Radius communication and data, and explains how to implement access control mechanisms to protect these servers.
Security Vulnerabilities
Radius servers are susceptible to various security vulnerabilities that could compromise the integrity and confidentiality of network access control. Here are some common vulnerabilities:
- Weak or Default Credentials: Using default or easily guessable passwords for the Radius server and its administrative accounts can expose the server to unauthorized access.
- Unencrypted Communication: Traditional Radius communication relies on UDP (User Datagram Protocol), which is an unencrypted protocol. This makes it vulnerable to eavesdropping and man-in-the-middle attacks where attackers can intercept and manipulate authentication requests and responses.
- Vulnerable Software: Outdated or unpatched Radius server software can contain known security flaws that attackers can exploit to gain unauthorized access or compromise the server’s functionality.
- Weak Access Control: Insufficiently configured access control lists (ACLs) can allow unauthorized users or devices to access the Radius server or its resources.
- Denial-of-Service (DoS) Attacks: Attackers can launch DoS attacks against the Radius server, overwhelming it with traffic and making it unavailable to legitimate users.
- Authentication Bypass: Attackers can exploit vulnerabilities in the Radius protocol or server implementation to bypass authentication and gain unauthorized access to network resources.
Securing Radius Communication and Data
Protecting Radius communication and data is crucial to maintaining the integrity and confidentiality of network access control. Here are some best practices for securing Radius:
- Use Strong Passwords and Multi-Factor Authentication (MFA): Employ strong passwords and implement MFA for administrative accounts to prevent unauthorized access to the Radius server.
- Enable Encryption: Utilize protocols like Transport Layer Security (TLS) or Secure Sockets Layer (SSL) to encrypt Radius communication, protecting it from eavesdropping and man-in-the-middle attacks. These protocols provide secure communication channels over the internet or other networks.
- Implement Access Control: Configure strict access control lists (ACLs) to restrict access to the Radius server based on user roles, IP addresses, or other criteria. This ensures that only authorized users and devices can communicate with the server.
- Regularly Update Software: Keep the Radius server software and all related components up-to-date with the latest security patches to address known vulnerabilities.
- Monitor for Anomalies: Implement monitoring tools to detect suspicious activity or anomalies in Radius traffic. This can help identify potential attacks and take timely action to mitigate the risks.
- Implement Secure Configuration: Configure the Radius server with secure settings, including disabling unnecessary services and ports, limiting the number of concurrent connections, and implementing strong authentication mechanisms.
Access Control Mechanisms
Implementing robust access control mechanisms is essential for protecting Radius servers from unauthorized access and ensuring secure network access control. Here are some key access control mechanisms:
- Role-Based Access Control (RBAC): RBAC assigns permissions to users based on their roles within the organization. This ensures that users only have access to the resources they need to perform their duties.
- Network Access Control (NAC): NAC is a security framework that enforces access control policies based on the identity, health, and security posture of devices attempting to connect to the network. This helps prevent unauthorized devices from accessing the network and ensures that all devices meet security standards.
- IP Address Filtering: Restricting access to the Radius server based on IP addresses can help prevent unauthorized access from specific networks or devices.
- Authentication and Authorization: Implement strong authentication and authorization mechanisms to verify the identity of users and devices attempting to access the Radius server and its resources. This can include multi-factor authentication, certificate-based authentication, and other secure authentication methods.
Radius Server Integration
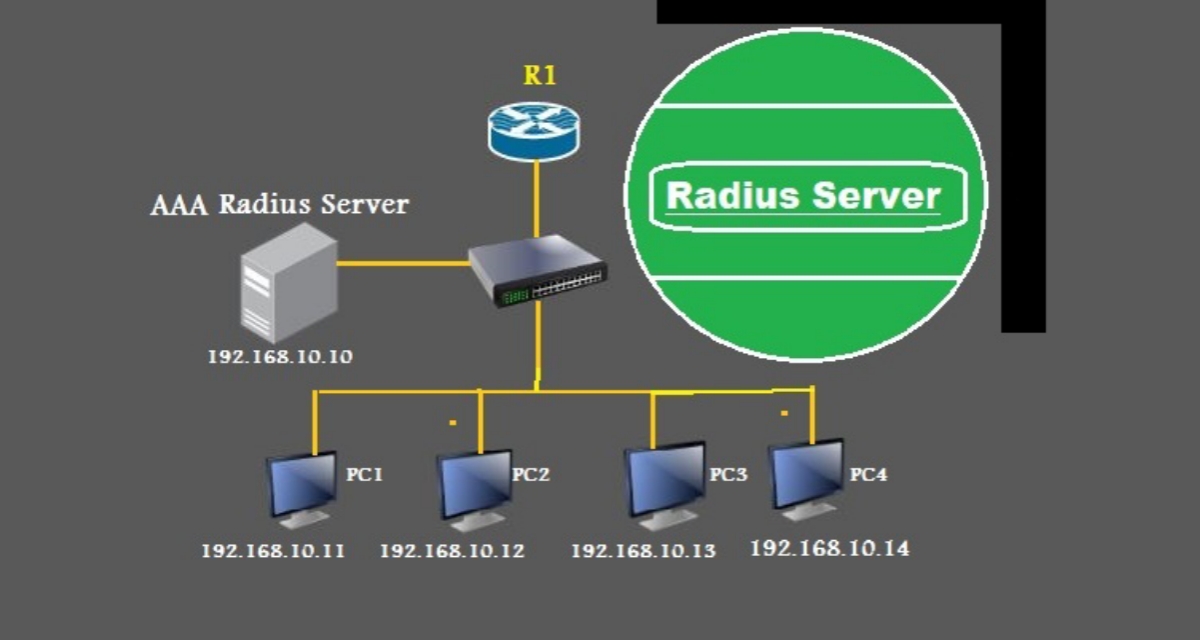
Radius servers are often integrated with other network security tools to enhance security and streamline operations. They work in conjunction with firewalls, intrusion detection systems (IDS), and other network security components to provide a comprehensive security solution.
Integration with Other Network Security Tools
The integration of Radius servers with other network security tools enables centralized authentication and authorization, improving network security and simplifying administration.
- Firewalls: Radius servers can be integrated with firewalls to enforce access control policies. When a user attempts to connect to the network, the firewall sends a request to the Radius server for authentication. The Radius server verifies the user’s credentials and authorizes access based on the configured policies. This integration ensures that only authorized users can access the network.
- Intrusion Detection Systems (IDS): Radius servers can be used to collect and analyze user activity data, which can be used by intrusion detection systems to identify potential security threats. The Radius server logs user login attempts, successful and failed logins, and other relevant information. This data helps IDS systems to detect suspicious activity and alert administrators.
- Virtual Private Networks (VPNs): Radius servers can be used to authenticate users connecting to a VPN. When a user connects to a VPN, the VPN server sends a request to the Radius server to authenticate the user. The Radius server verifies the user’s credentials and grants access to the VPN.
Role in Multi-Factor Authentication (MFA) Systems
Radius servers play a crucial role in multi-factor authentication (MFA) systems by providing a centralized authentication mechanism that can be used to enforce MFA policies.
- Centralized Authentication: Radius servers provide a central point for authentication, making it easier to manage MFA policies across different network devices and applications.
- Flexible Authentication Methods: Radius servers support various authentication methods, including passwords, one-time passwords (OTPs), biometrics, and hardware tokens. This flexibility allows organizations to choose the most appropriate MFA methods for their specific needs.
- Policy Enforcement: Radius servers can be configured to enforce MFA policies based on user roles, device type, or network location. For example, an organization may require MFA for all users accessing sensitive data or for users connecting from untrusted networks.
Use in Network Access Control (NAC)
Radius servers are essential components of network access control (NAC) systems, which enforce security policies based on user identity, device health, and network location.
- User Authentication: Radius servers authenticate users connecting to the network, ensuring only authorized users can access network resources.
- Device Health Checks: Radius servers can be integrated with network devices to perform device health checks, ensuring that devices meet security requirements before granting access.
- Network Access Control: Radius servers enforce network access control policies based on user identity, device health, and network location. For example, a NAC system may restrict access to certain network segments based on the user’s role or the device’s operating system.
Radius Server Management
Effective Radius server management is crucial for maintaining a secure and reliable network infrastructure. It involves a comprehensive approach to monitoring, troubleshooting, and optimizing server performance.
Monitoring Radius Servers
Monitoring Radius servers is essential for identifying potential issues and ensuring their smooth operation. This involves tracking key performance indicators (KPIs) and analyzing logs for anomalies.
- Server Resource Utilization: Monitoring CPU usage, memory consumption, disk space, and network bandwidth helps detect resource bottlenecks and optimize server performance.
- Authentication and Authorization Success Rates: Tracking the success rate of authentication and authorization requests provides insights into the efficiency of the Radius server and potential access control issues.
- Log Analysis: Regularly reviewing server logs for errors, warnings, and suspicious activity helps identify and address security vulnerabilities and performance problems.
Troubleshooting Radius Servers
Troubleshooting Radius server issues requires a systematic approach to identify and resolve problems. This involves gathering information, analyzing logs, and implementing appropriate solutions.
- Gather Information: Collect relevant data, such as error messages, system logs, and network configurations, to pinpoint the root cause of the issue.
- Analyze Logs: Scrutinize server logs for error codes, timestamps, and relevant details that provide clues about the problem.
- Verify Network Connectivity: Ensure that the Radius server has proper network connectivity to the network devices and client systems.
- Check Authentication and Authorization Settings: Verify the accuracy and consistency of authentication and authorization policies and configurations.
Optimizing Radius Server Performance
Optimizing Radius server performance involves implementing strategies to improve its efficiency and responsiveness. This can involve adjusting server settings, configuring network traffic, and implementing security measures.
- Optimize Server Configuration: Fine-tune server settings, such as memory allocation, CPU affinity, and network buffer sizes, to enhance performance.
- Manage Network Traffic: Implement network traffic shaping and prioritization to ensure smooth Radius server operation.
- Implement Security Measures: Utilize firewalls, intrusion detection systems (IDS), and access control lists (ACLs) to protect the Radius server from unauthorized access and malicious attacks.
Tools for Radius Server Management
Several tools and techniques can be used for managing Radius servers effectively. These tools provide comprehensive monitoring, troubleshooting, and optimization capabilities.
- Network Management Systems (NMS): NMS platforms like SolarWinds Network Performance Monitor, ManageEngine OpManager, and PRTG Network Monitor offer centralized monitoring and management capabilities for Radius servers, providing real-time insights into server health and performance.
- Log Analysis Tools: Log analysis tools like Splunk, Graylog, and ELK stack help analyze server logs, identify patterns, and detect anomalies, providing valuable information for troubleshooting and security investigations.
- Performance Monitoring Tools: Performance monitoring tools like JMeter, LoadRunner, and Gatling can be used to test the performance of Radius servers under various load conditions, identifying bottlenecks and areas for optimization.
Recommendations for Radius Server Optimization
To ensure optimal Radius server performance, consider these recommendations:
- Dedicated Hardware: Allocate dedicated hardware resources, such as a separate server or virtual machine, for the Radius server to minimize resource contention and improve performance.
- Regular Maintenance: Perform regular maintenance tasks, including software updates, security patches, and system optimization, to ensure the Radius server remains secure and efficient.
- Load Balancing: Implement load balancing techniques to distribute traffic across multiple Radius servers, improving scalability and fault tolerance.
- Security Best Practices: Adhere to security best practices, such as using strong passwords, enabling two-factor authentication, and regularly auditing access controls, to protect the Radius server from unauthorized access and attacks.
Radius Server Standards and Protocols
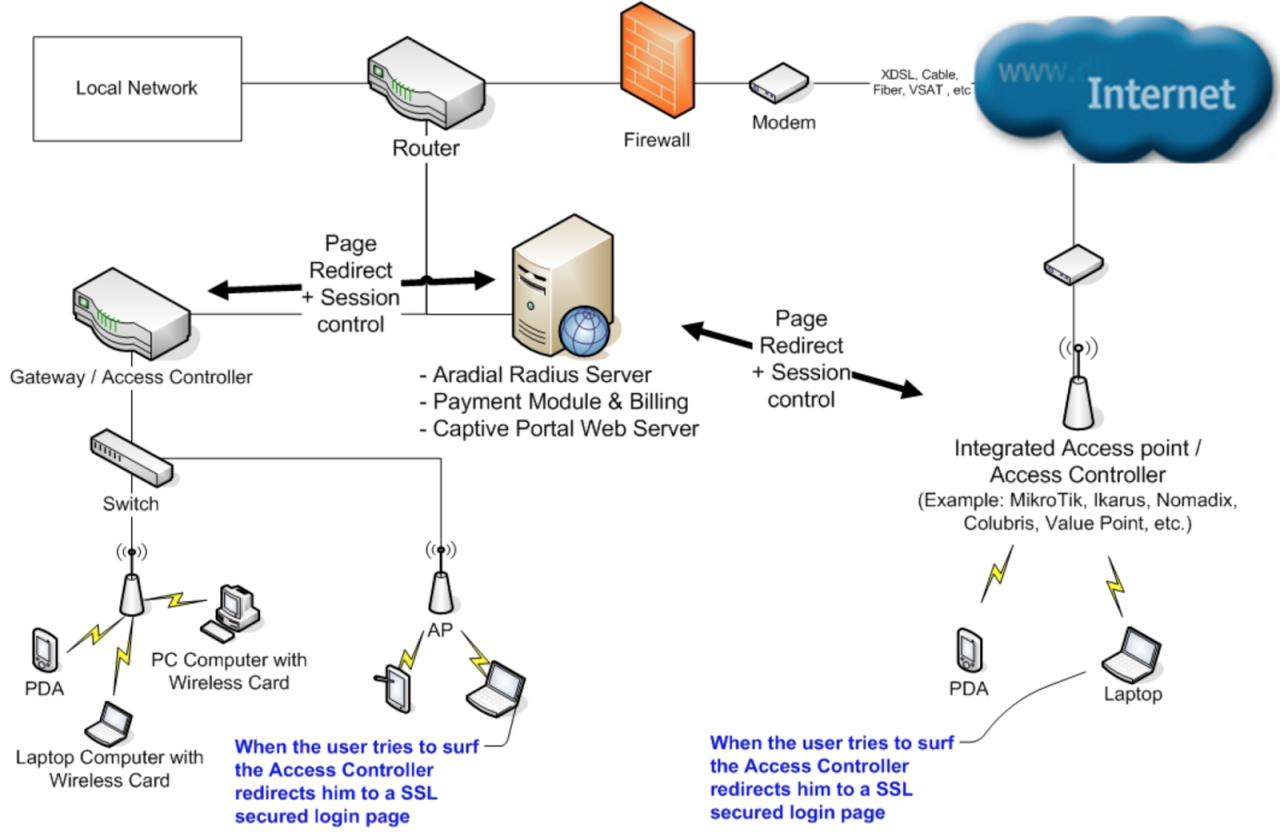
The Radius protocol operates on a client-server model, facilitating communication between network access servers (NAS) and a central Radius server. This communication relies on a set of standards and protocols that ensure interoperability and security.
Radius Protocol
The Radius protocol defines the communication format and message structure used between NAS and Radius servers. It uses User Datagram Protocol (UDP) for transport and operates on port 1812 for authentication and 1813 for accounting. Each message consists of a header and attributes, including user information, authentication data, and accounting details.
Diameter Protocol
The Diameter protocol is a newer and more advanced protocol that aims to replace Radius. It provides several enhancements, including improved security, scalability, and support for more complex network services. Diameter uses Transport Control Protocol (TCP) for transport and operates on port 3868.
Evolution of Radius Standards, Radius server
The Radius standard has evolved over time, introducing new features and addressing security concerns. The initial version, Radius v1, lacked strong encryption mechanisms, making it vulnerable to attacks. Radius v2 introduced encryption using the Message Digest 5 (MD5) algorithm, enhancing security but still leaving room for vulnerabilities. The latest version, Radius v3, implemented stronger encryption using the Advanced Encryption Standard (AES), significantly improving security.
Latest Advancements in Radius Technology
The Radius protocol continues to evolve, incorporating new technologies and addressing emerging security threats.
- Support for modern authentication methods: Radius is being integrated with modern authentication methods like OAuth 2.0 and OpenID Connect, enhancing security and user experience.
- Integration with cloud services: Radius is increasingly being used to manage access to cloud-based resources, providing a centralized authentication and authorization mechanism for hybrid environments.
- Improved security features: Newer versions of Radius implement advanced security features like Transport Layer Security (TLS) encryption, ensuring secure communication between NAS and Radius servers.
Radius Server Future Trends
The realm of Radius server technology is constantly evolving, driven by advancements in networking, security, and cloud computing. This evolution promises to shape the future of authentication, authorization, and accounting for network access.
Impact of Cloud Computing and Virtualization
The adoption of cloud computing and virtualization has a profound impact on Radius server deployment and management.
- Cloud-based Radius servers offer scalability and flexibility, allowing organizations to easily adjust their capacity based on changing needs. These servers are hosted by third-party providers, eliminating the need for on-premises infrastructure and maintenance.
- Virtualization allows for the creation of multiple Radius servers on a single physical machine, improving resource utilization and reducing hardware costs. Virtualized Radius servers can be easily deployed, scaled, and migrated, offering greater agility and resilience.
Future Directions for Radius Server Security and Management
The evolving threat landscape necessitates continuous improvements in Radius server security and management.
- Enhanced Authentication Methods: Incorporating stronger authentication methods, such as multi-factor authentication (MFA) and biometrics, can significantly enhance Radius server security. MFA requires users to provide multiple forms of identification, making it more difficult for unauthorized individuals to gain access.
- Advanced Access Control: Implementing fine-grained access control mechanisms, such as role-based access control (RBAC), allows organizations to define specific permissions for different users and groups, minimizing the risk of unauthorized actions.
- Automated Security Monitoring: Implementing automated security monitoring tools can help detect and respond to potential threats in real time. These tools can analyze network traffic, identify suspicious activities, and trigger alerts to security teams.
- Regular Security Audits: Regular security audits are essential to identify and address vulnerabilities in Radius server configurations and software. These audits should be conducted by qualified security professionals who can assess the server’s security posture and recommend improvements.
Summary
In the ever-evolving landscape of cybersecurity, Radius servers remain indispensable tools, ensuring secure access to your network and protecting your valuable data. Understanding their intricacies and implementing best practices for their management is crucial for maintaining a robust and resilient network security posture. As technology advances, Radius servers will continue to adapt, playing a critical role in safeguarding the digital world we inhabit.
Radius servers are essential for network authentication and authorization, ensuring secure access to resources. While you might not think of them as a creative outlet, the process of configuring a Radius server can be surprisingly similar to creating a beautiful macrame wall hanging, requiring careful planning, attention to detail, and a bit of artistry.
If you’re looking for a fun and creative project, check out this macrame diy guide, and then you can return to the world of Radius servers with a renewed appreciation for the intricacies of network security.